Kerberos Authentication
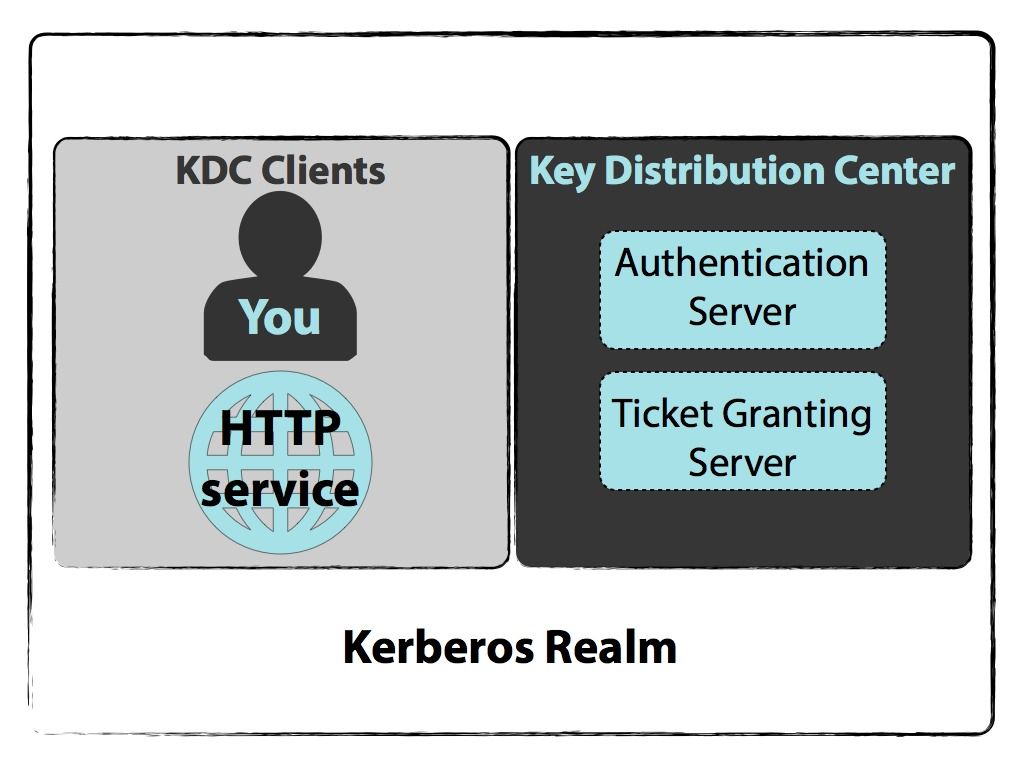
Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. You need to change the domain information to reflect your Network environment.

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux
The Oracle Kerberos authentication adapter utilities are designed for an Oracle client with Oracle Kerberos authentication support installed.

Kerberos authentication. Read on to learn what Kerberos authentication is and how it protects both end-users and systems. Once the request arrives on-premises the Azure AD Application Proxy connector issues a Kerberos ticket on behalf of the user by interacting with the local Active Directory. Basically Kerberos is a network authentication protocol that works by using secret key cryptography.
Kerberos works with the concept of tickets which are encrypted and can help reduce the amount of times passwords need to be sent over the network. Kerberos is available in many commercial products as well. MongoDB Enterprise only supports the MIT implementation of Kerberos.
The Kerberos KDC returns a TGT and a session key to the PC Client. Kerberos is een standaard authenticatieprotocol dat ervoor zorgt dat gebruikers van een netwerk zich op een veilige manier kunnen aanmelden en hun identiteit kunnen bewijzen zonder zich telkens opnieuw te moeten aanmelden. Kerberos at its simplest is an authentication protocol for clientserver applications.
The protocol was initially developed by MIT in the 1980s and was named after the mythical three-headed dog who guarded the underworld Cerberus. Kerberos is an authentication protocol that can provide secure network login or SSO for various services over a non-secure network. This protocol keeps passwords away from insecure networks at all times even during user verification.
Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. However it does not prevent a passive attacker from sniffing the clients encrypted timestamp message to the KDC. Each user and service on the network is a principal.
These are the steps in Kerberos Authentication. A free implementation of this protocol is available from the Massachusetts Institute of Technology. Kerberos allows MongoDB and applications to take advantage of existing authentication infrastructure and processes.
Kerberos ˈkɜːrbərɒs is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. The Apache server was configured to request password authentication to access the directory named TEST. Thus Kerberos pre-authentication can prevent the active attacker.
I also have a lot of storage devices eg QNAPs which are only monitored via SNMP but I can see NTLM Authentication attempts using a domain user from the probe server to. A ticket request for the application server is sent to the Kerberos KDC. Lets see how all of this works.
Kerberos authentication protects user credentials from hackers. It might also use NTLM which is also a provider in windows authentication. Kerberos is an authentication protocol for clientserver applications.
Microsoft introduced their version of Kerberos in Windows2000. This allows for strong and secure authentication without transmitting passwords. Services that run on Windows operating systems can impersonate a client computer when.
The Kerberos delegation flow in Azure AD Application Proxy starts when Azure AD authenticates the user in the cloud. Kerberos is an industry standard authentication protocol for large clientserver systems. I have seen the other threads where it has been stated that PRTG does not support Kerberos with WMI.
Kerberos is a network authentication protocol. Clients authenticate with a Key Distribution Center and get temporary keys to access locations on the network. A Ticket-Granting Ticket TGT request is sent to a Kerberos KDC.
If the attacker can sniff that full packet he can brute force it offline. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. To mitigate this problem it is.
Its designed to provide secure authentication over an insecure network. Kerberos maakt een beperkte vorm van Single Sign-on mogelijk. Het MIT ontwikkelde Kerberos als beveiliging voor hun Project Athena en vernoemde het naar het Griekse mythologische karakter Kerberos.
The benefits gained by using Kerberos for domain-based authentication are. PC Client logs on the domain. Using Kerberos authentication within a domain or in.
Connecting to an Oracle Database Server Authenticated by Kerberos After Kerberos is configured you can connect to an Oracle database server without using a user name or password. Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. In Kerberos Authentication server and database is used for client authentication.
In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication. The Apache service was configured to authenticate user accounts using Kerberos. This request consists of the PC Client TGT and an authenticator.
Kerberos Components and MongoDB.

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony

Kerberos Architecture Computer Help Windows Server Microsoft

Mongodb Authentication With Kerberos Regular Expression Data Storage Reading

Kerberos Authentication Architecture Ile Ilgili Gorsel Sonucu Cryptography Architecture Kas

Optimizing Ntlm Authentication Flow In Multi Domain Environments Cyber Security Optimization Computer Server

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cached In 2021 Windows Client Fails Clients

Pin On Storage

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base

Part3 Troubleshooting Kerberos Authentication And Things To Check When It Fails Fails Microsoft Dynamics Recruitment

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cached In 2021 Windows Client Fails Clients

Using Sql Service Broker For Asynchronous External Script R Python Execution In Oltp Systems Sql Relational Database Management System Sql Server
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Configuring Kerberos Authentication In Different Browsers Browser Internet Options Web Server

Kerberos Architecture Computer Help Windows Server Microsoft

Sap Hana Authentication Methods For Verification Of User Identity Username Password Kerberos Saml Sap Logon Tickets And Assertion Sap Hana Markup Language

Register A Spn For Sql Server Authentication With Kerberos Sql Server Microsoft Sql Server Sql